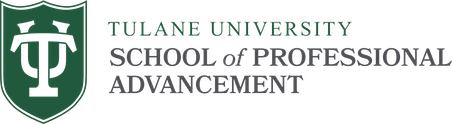IoT Security Challenges and Threats
As technology companies continue to develop and improve IoT devices, one challenge will persist: how to keep devices safe and secure.
To learn more, check out the infographic below created by Tulane University’s School of Professional Advancement Information Technology program.
IoT Security Challenges
As the IoT expands, so do the number of challenges pertaining to device security. One of the chief challenges involves supporting complex and evolving security algorithms despite limitations in a device’s memory and computing resources. Another challenge involves the scaling and managing of billions of devices in the IoT ecosystem. Identifying endpoints in a scalable manner poses another challenge, as does identifying the roles and responsibilities of vendors, owners, and users in a multiparty network. Finally, protecting mobile devices from theft is a challenge that must be addressed.
IoT Security Threats
There are a host of threatening issues that could conceivably cause significant chaos within the IoT. Some of these issues directly take advantage of the IoT’s design. For example, a threat called spoofing occurs when an attacker breaches a lower-level device with little or no security and gains access to a network with protected devices, which is then tricked into believing the intruder is encrypted.
Other threats utilize IP disruptions to infiltrate a system. One of these threats is smurfing, which is a denial-of-service attack that uses IP spoofing to overwhelm a server and prevent it from responding to legitimate requests. Another denial-of-service attack is IP/ICMP fragmentation, a threat that causes an IP to become fragmented, transmitted across a network, and then reassembled to overwhelm the network.
Intrusion-related threats can also potentially disrupt IoT security. With the sniffing tactic, a malicious security tag pretends to be a valid tag and gains unauthorized access to a network. A somewhat similar threat is known as reconnaissance, where an intruder gains access to the network to gather information about vulnerabilities. Another threat known as the man in the middle features an attacker that connects between two endpoints and intercepts and eavesdrops on a conversation. A fourth threat in this vein is the rogue device, in which devices remain connected to a system without having permission to access and operate in the network.
There is also a range of group threats that needs to be considered when developing an IoT security strategy. The first group is “script kiddies,” which are inexperienced hackers that use simple methods to hack unprotected webcams, take over home control systems, steal content, and engage in other forms of hacking. Another group is organized crime, which engage in espionage, sabotage, and the theft of intellectual property. Finally, there are agents that engage in large-scale cyber attacks that target nuclear plants, traffic monitoring, railways, and critical infrastructure.
Protecting IoT Data and Privacy
IoT device manufacturers are responsible, to a certain extent, for keeping devices safe and secure. However, consumers must also take steps to protect their devices.
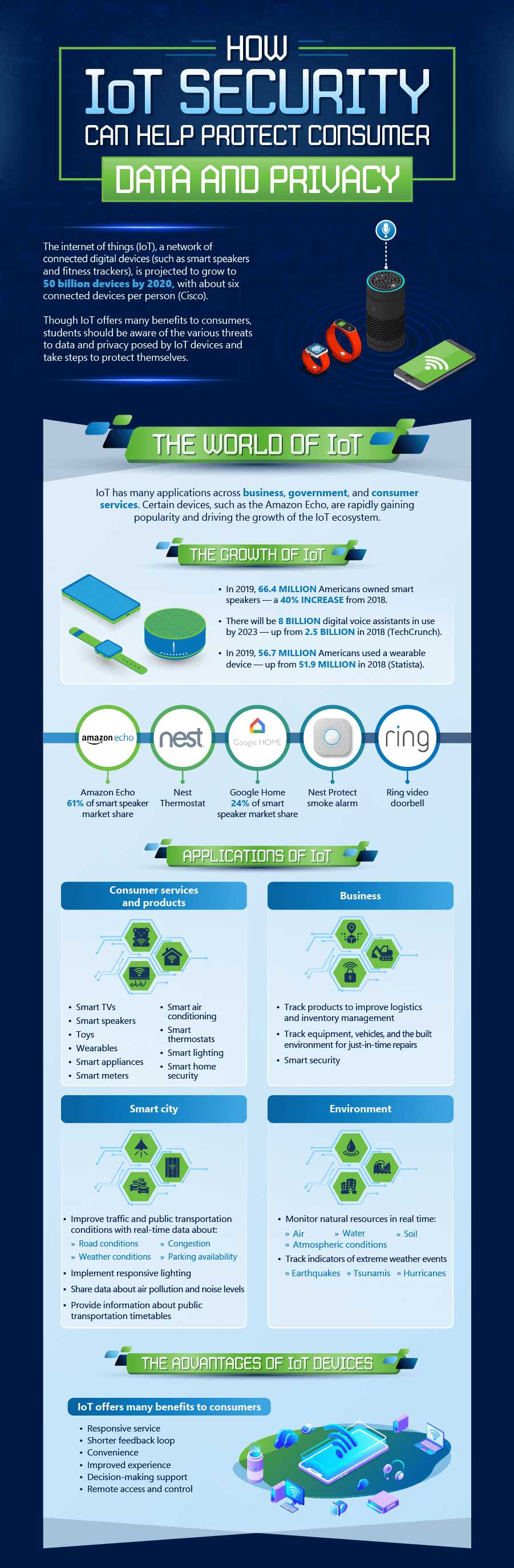
The Foundations of a Secure IoT
One of the key components of a secure IoT is authentication. Before gaining access to the IoT infrastructure, devices or endpoints must provide identification by one of several means. These can include radio-frequency identification (RFID), a shared secret such as a cryptographic key or private data, digital certificates that use the X.509 public key infrastructure standard, and the use of a media access control (MAC) address of the endpoint, like a unique identifier for an Ethernet or network adapter over a network, physical address, hardware address, or burned-in address.
Another key component for IoT security is authorization. This is where a device’s access throughout the network and the ability to share information is controlled by an authorization layer. This step can be used to establish a trust relationship.
A third foundational component is network enforced policy. In this component, the elements responsible for routing and transporting endpoint traffic are governed by established protocols and mechanisms.
Finally, security analytics offers a foundational means for IoT security. In this strategy, analytics algorithms and security intelligence processes identify threats by collecting data from multiple sources and applying statistical models and security profiles.
Tips for Protecting IoT Devices
As with many tech-driven concepts, changing default passwords and setting strong passwords for IoT devices and your Wi-Fi router can be essential to keeping them protected. It’s also important to add different layers of protection to the accessibility process, such as implementing two-factor authentication, using a strong encryption method for Wi-Fi, or creating an unusual name for your router to protect personal identifiers. Unplugging unused devices and disabling unused features and Universal Plug and Play (UPnP) can lower the number of network entry or connection points. It’s also worth considering newer device models for enhanced security; when these are incorporated, it’s important to check the default privacy settings on IoT devices and consider changing them for more protection. It’s also important to update devices regularly regardless of newness. Finally, while its important to create a separate Wi-Fi network for guests, it’s wise to avoid connecting to public Wi-Fi networks.
Conclusion
The future of technology will see an advanced IoT ecosystem that connects a myriad of devices across many different environments. Consumers and students should educate themselves on a device’s vulnerabilities before making a purchasing decision and always take the necessary steps to protect their data and privacy.